

Enabling a certificate revocation list in Secure Sockets Layer
This section provides information on identifying directives for certificate revocation list (CRL) and those supported in global servers and virtual hosts. Links to related topics appear at the end of this section.
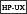
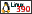
 Certificate revocation lists are not supported on
HP and Linux for S/390 operating systems.
Certificate revocation lists are not supported on
HP and Linux for S/390 operating systems.
- Identifying directives needed to set up certificate revocation list
- Identifying directives supported in global server and virtual host
- Finding related information
Certificate revocation provides the ability to revoke a client certificate given to the IHS server by the browser when the key becomes compromised or when access permission to the key gets revoked. CRL represents a database which contains a list of certificates revoked before their scheduled expiration date.
If you want to enable certificate revocation in the IBM HTTP Server, publish the CRL on a Lightweight Directory Access Protocol (LDAP) server. Once the CRL is published to an LDAP server, you can access the CRL using the IBM HTTP Server configuration file. The CRL determines the access permission status of the requested client certificate.
Identifying directives needed to set up certificate revocation list
The SSLClientAuth directive can include two options at once:
- SSLClientAuth 2 crl
- SSLClientAuth 1 crl
The CRL option, turns CRL on and off inside an SSL virtual host. If you specify crl as an option, then you elect to turn CRL on. If you do not specify crl as an option, then CRL remains off. If the first option for SSLClientAuth equals 0/none, then you cannot use the second option, crl. If you do not have client authentication on, then CRL processing does not take place.
Identifying directives supported in global server and virtual host
Global server and virtual host support the following directives:
- SSLCRLHostname: The IP Address and host of the LDAP server, where the CRL database resides.
- SSLCRLPort: The port of the LDAP server where the CRL database resides; the default equals 389.
- SSLCRLUserID: The user ID to send to the LDAP server where the CRL database resides; defaults to anonymous if you do not specify the bind.
- SSLStashfile: The fully qualified path to file where the password for the user name on the LDAP server
resides. This directive is not required for an anonymous bind. Use when you specify a user ID.
Use the sslstash command, located in the bin directory of IBM HTTP Server, to create your
CRL password stash file. The password you specify using the sslstash command should equal the one you use
to log in to your LDAP server.
Usage: sslstash [-c] <directory to password file and file name> <function name> <password>
where:- -c: Creates a new stash file. If not specified, an existing file updates.
- File: Represents the fully qualified name of the file to create, or update.
- Function: Indicates the function for which to use the password. Valid values include crl, or crypto.
- Password: Represents the password to stash.
| Finding related information |
(Back to the top)